How to perform a pentest?
Table of contents
Introduction
A penetration test, colloquially known as a pen test, is an authorized simulated cyber attack on a computer system, performed to evaluate the security of the system.
The test is performed to identify both weaknesses, including the potential for unauthorized parties to gain access to the system's features and data, as well as strengths, enabling a full risk assessment to be completed.
There are to types of targets:
Insights provided by the penetration test can be used to fine-tune your WAF(Web Application Firewall) security policies and patch detected vulnerabilities.
The test is performed to identify both weaknesses, including the potential for unauthorized parties to gain access to the system's features and data, as well as strengths, enabling a full risk assessment to be completed.
There are to types of targets:
- White box: Provides background and system information.
- Black box: Provides only basic or no information except the company name.
A gray box is what we define as a combination of these two.
Insights provided by the penetration test can be used to fine-tune your WAF(Web Application Firewall) security policies and patch detected vulnerabilities.
Penetration Test Stages
The pen testing process can be broken down into five stages.
- Planning and reconnassance:
- Defining the scope and goals of a test, including the systems to be addressed and the testing methods to be used.
- Gathering intelligence to better understand how a target works and its potential vulnerabilities.
- Scanning:
- Understand how the target application will respond to various intrusion attempts.
- Gaining access:
- This stage uses web application attacks to uncover a target’s vulnerabilities.
- Maintaining access:
- The goal of this stage is to see if the vulnerability can be used to achieve a persistent presence in the exploited system.
- Analysis:
- Specific vulnerabilities that were exploited.
- Sensitive data that was accessed.
- The amount of time the pen tester was able to remain in the system undetected.
Let's try a PenTestTool
In this case, my go to one will be:
This is much more simple than it may look, only an address is needed to perform.
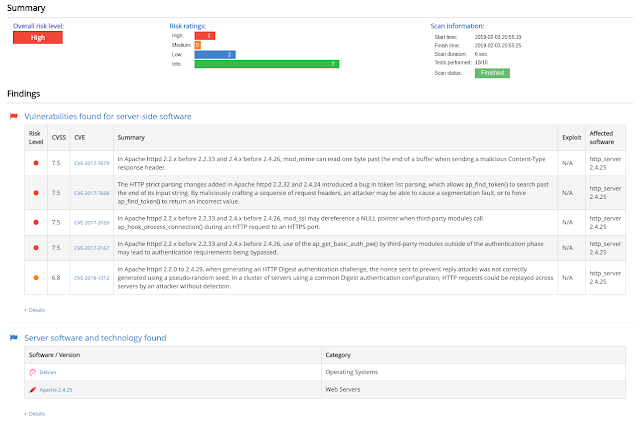
Once performed all we have to do is to analyze the following graphics:
It is quite clear that apache is not well secured in our case and that is leading to a lot of security holes, but, a pentesting always offers possible solutions so let's be smart and follow them(That will be private but here is the solutions chart).
What do you think? Will you use it?
This is much more simple than it may look, only an address is needed to perform.
Once performed all we have to do is to analyze the following graphics:
It is quite clear that apache is not well secured in our case and that is leading to a lot of security holes, but, a pentesting always offers possible solutions so let's be smart and follow them(That will be private but here is the solutions chart).
What do you think? Will you use it?
Thank you for reading my amateur tutorial and I hope we'll keep improving together!



Comentarios
Publicar un comentario